Bottom line: Ransomware remains a persistent threat, proving resilient against even the most determined law enforcement efforts. Much like cockroaches, these groups demonstrate an uncanny ability to adapt and endure in the face of adversity. That's why it is essential for organizations to protect themselves by implementing proactive security measures and developing comprehensive response plans.
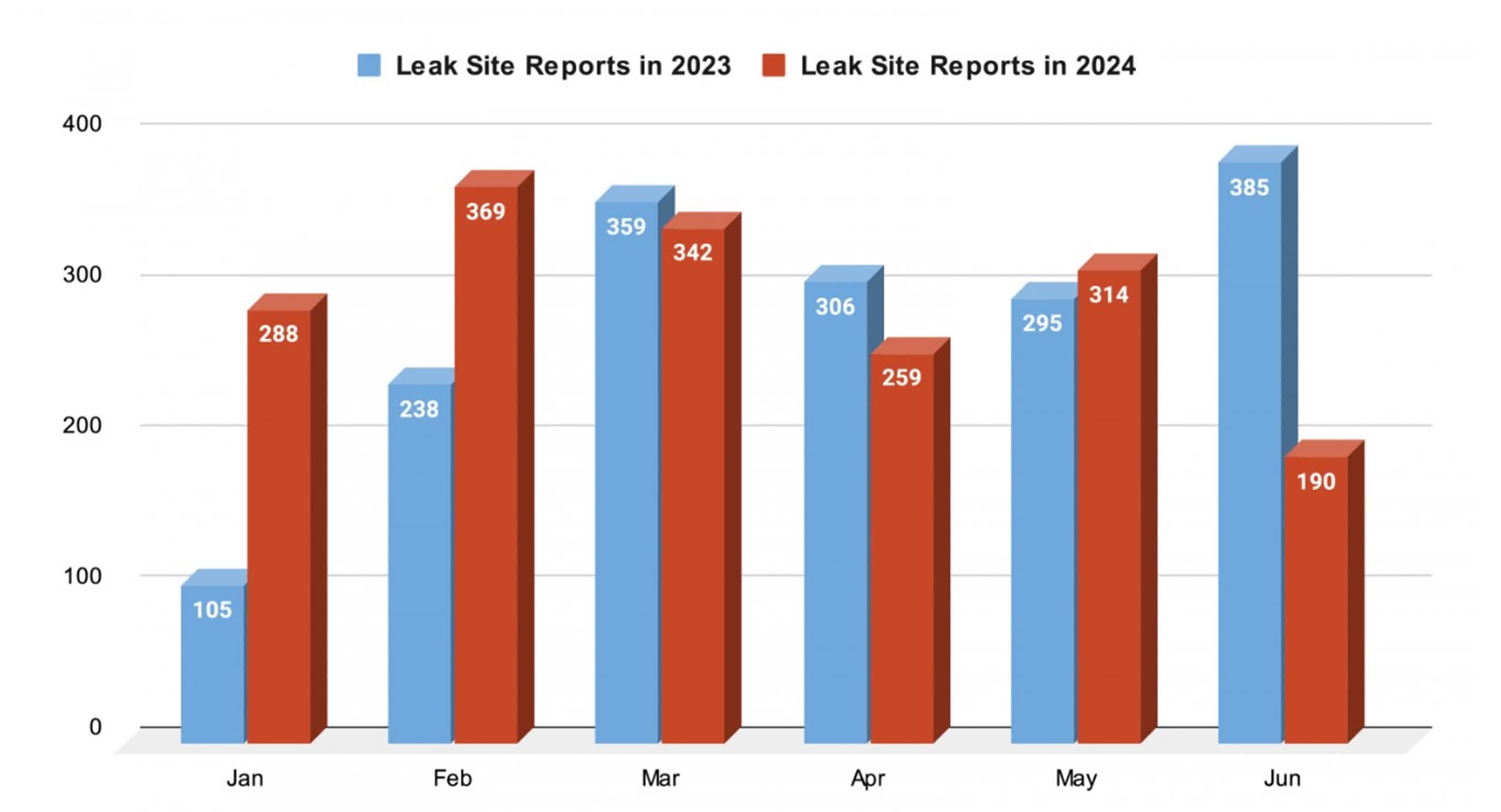
Ransomware attacks continue to plague global industries, with Unit 42's recent analysis revealing a troubling rise in activity. During the first six months of 2024, Unit 42, the threat intelligence team of Palo Alto Networks, monitored 53 ransomware groups' leak sites, observing 1,762 posts – a 4.3% increase from the same period the previous year. This increase underscores the persistent threat posed by these cybercriminals, despite ongoing law enforcement efforts to dismantle their operations.
Despite facing a law enforcement takedown in February, LockBit 3.0 remains the most prolific ransomware group in early 2024. Known as Flighty Scorpius in Unit 42's tracking system, LockBit 3.0 claimed 325 victims in the first half of the year. This is significant, even though it represents a decrease from the 928 victims in all of 2023.
Unit 42's method of categorizing ransomware groups involves pairing a modifier with a constellation, aiding in the precise identification and monitoring of these threat actors. For instance, LockBit 3.0 is dubbed "Flighty Scorpius," while BlackCat is referred to as "Ambitious Scorpius."
The top six ransomware groups were responsible for over half of the infections observed. Following LockBit 3.0, the Play group, known as Fiddling Scorpius, reported 155 victims. The 8base group, also known as Squalid Scorpius, and Akira, referred to as Howling Scorpius, each accounted for 119 victims.
BlackBasta, identified as Dark Scorpius, was responsible for 114 attacks, while Medusa, or Transforming Scorpius, affected 103 victims.
Play advanced from fourth place in 2023 to second in 2024's first half, while 8base, a relative newcomer believed to be a rebrand of Phobos, rose to third place.
Interestingly, two prominent ransomware groups from 2023 did not make the top six list in the first half of 2024. ALPHV/BlackCat, previously ranked second with 388 victims, and CLOP, third with 364 victims, were notably absent from the top ranks.
Unit 42's data also highlights the industries most affected by ransomware attacks. Manufacturing emerged as the most impacted sector, accounting for 16.4% of observed posts on ransomware leak sites.
Healthcare followed with 9.6%, a sector particularly vulnerable due to its sensitivity to disruptions and downtime. The construction industry accounted for 9.4% of the ransomware posts, making it the third most impacted sector.
Geographically, the United States was the hardest hit, with 917 compromises, representing 52% of total attacks. Other heavily impacted nations included Canada, the UK, Germany, Italy, France, Spain, Brazil, Australia, and Belgium.