In brief: In the hours following Friday's global Windows BSOD, many wondered why CrowdStrike software was allowed full Windows kernel access. Microsoft now claims that a 15-year-old agreement with European regulators ties its hands on the issue, potentially leaving Windows-based enterprise systems vulnerable to similar catastrophes in the future.
Microsoft has provided additional information regarding the scale of last week's global CrowdStrike meltdown and how IT professionals can repair the damage. However, the company's options to prevent similar incidents are somewhat limited.
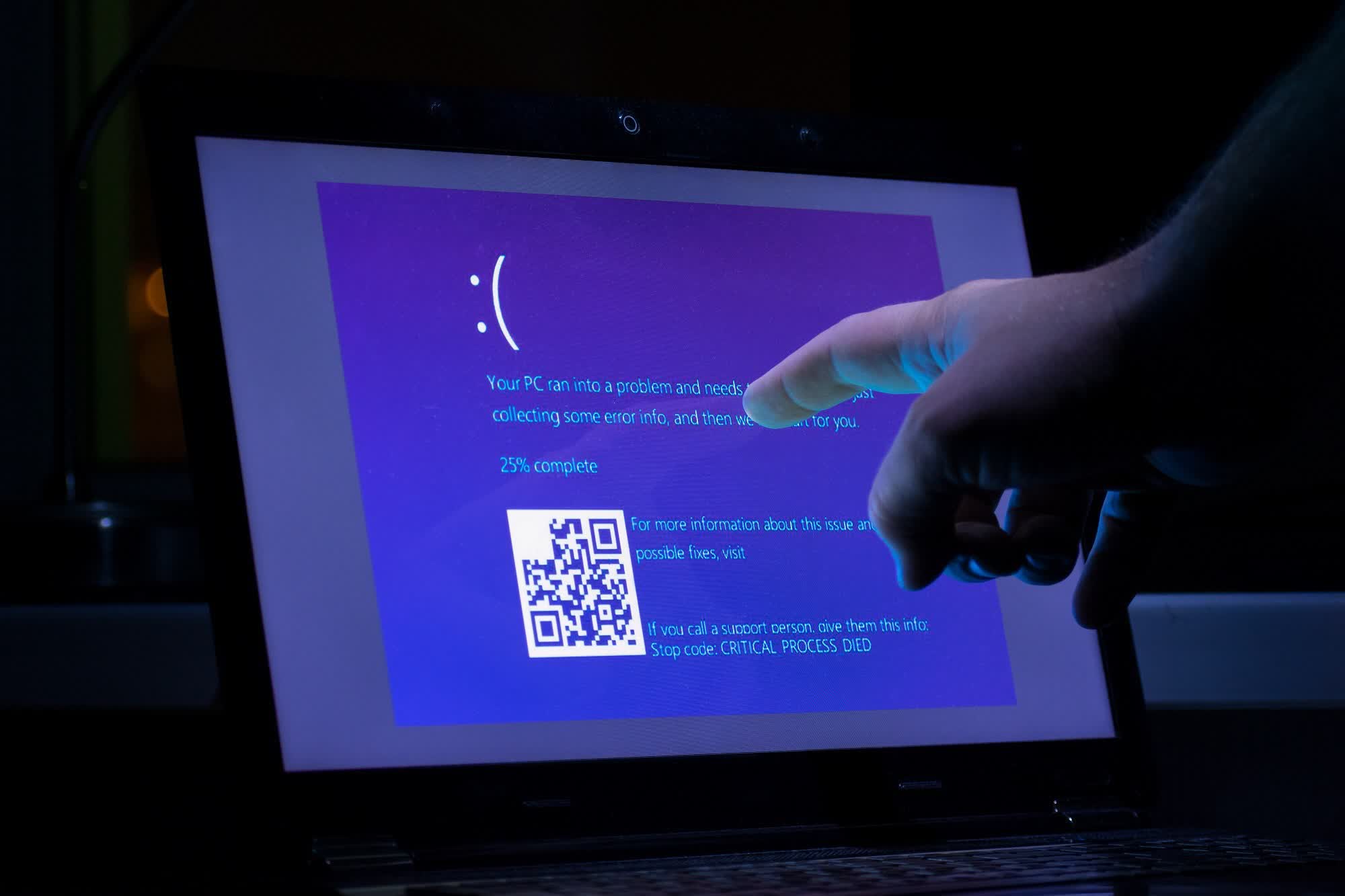
Although CrowdStrike fixed the faulty patch that brought businesses worldwide offline on Friday, many are still rebooting their systems or catching up with the resulting backlogs. Microsoft has provided a recovery tool with detailed instructions to facilitate repairs.
The software can create Windows recovery media or help a PC boot into safe mode. It requires a USB drive with between one and 32 GB of storage space and at least 8 GB of free space on a 64-bit Windows client. The process will format the USB drive to FAT32.
Microsoft claims CrowdStrike's meltdown impacted 8.5 million devices. While this number represents less than one percent of all Windows systems, their presence in the enterprise sector was significant enough to paralyze air traffic, hospitals, and other vital infrastructure.
Although the problem stems from CrowdStrike's software, a Wall Street Journal report indicates that Microsoft is taking most of the blame, as the company's infamous BSOD was the public face of the disaster. Many affected businesses and users had likely never heard of CrowdStrike before July 19.

Those in the know quickly blamed the software's level 0 kernel access to Windows, which allowed the error to hit the operating system's deepest layer. In contrast, Apple doesn't give third-party developers full kernel access, and its OS dodged the global meltdown.
In response, Microsoft told WSJ that it can't legally block third-party developers from gaining full kernel access due to a 2009 pact with the European Commission. A document on the company's website titled, "Microsoft Interoperability Undertaking," states that developers must be granted the same level of access to the operating system that Microsoft enjoys.
As long as the agreement stands, companies like CrowdStrike must voluntarily refrain from accessing the Windows kernel. It isn't uncommon for developers to draw scrutiny for invoking kernel-level system access. Hopefully, the CrowdStrike incident will bring more attention to this issue.